TSA Airport Access Security Requirements
The Issue
Airport Security Program Requirements
It is not unusual for pilots relocating their aircraft from one airport to another, or for tenants at an airport that is initiating new or larger commercial service, to encounter different security requirements. Under Transportation Security Administration (TSA) security regulations, airports are required to have a complete TSA-approved Airport Security Program (ASP) when scheduled airlines operate aircraft with 61 or more seats. Airport management may also be required to conduct security background checks and issue identification badges to hundreds of employees and other personnel authorized to enter movement areas, including tenant aircraft owners. These requirements can become tricky for both transient pilots and airport management because transient pilots lack locally issued security credentials.
Airports are responsible to ensure only those properly badged individuals enter the Air Operations Area (AOA). This responsibility is sometimes delegated to Fixed Base Operators (FBO), especially at the general aviation ramp to escort transient pilots. As a result, in some cases, transient pilots are forced to purchase unwanted services from the FBO or charged for a security fee because that is the only way to egress and ingress the general aviation ramp.
It is important to understand that there are alternative methods that are less onerous and still meet TSA requirements while being friendly to general aviation.
Lack of Transparency
Each airport is unique, and general aviation tenants should always be a part of the planning process for security-related matters that may affect their operations. The TSA works with the airport management to craft an ASP that fits that airport.
However, transient and based pilots, AOPA and the public do not have access to the specific requirements that govern airport security nor to finalized ASPs. This is because the information is considered Sensitive Security Information (SSI). SSI is not classified information; yet, there are specific handling procedures. More information can be found here. AOPA has always advocated that TSA Security Directives should be publicly circularized within 180 days of taking effect so as to allow public comment and to promote reasonable transparency.
Airport Security Areas and Basic Requirements
The TSA has issued regulations governing the security of airports with commercial service to ensure aircraft operations are secure. At most of these airports, general aviation has a significant presence. The governing regulation, 49 C.F.R. Part 1542, details how each airport operator is required to have a security program and must establish certain security areas.
At TSA-regulated airports, security related areas include: the Secured Area, Air Operations Area (AOA), Security Identification Display Area (SIDA), Sterile Area, and Airport Tenant Security Program (ATSP) Area.
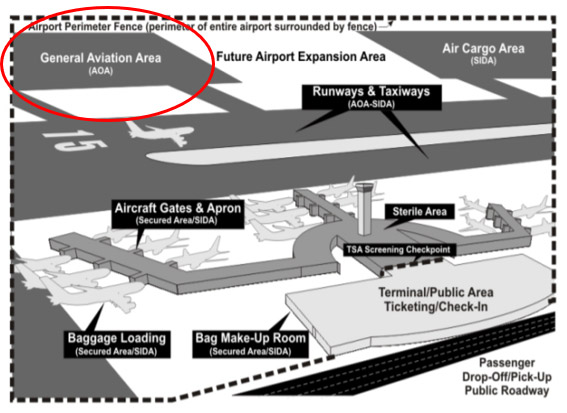
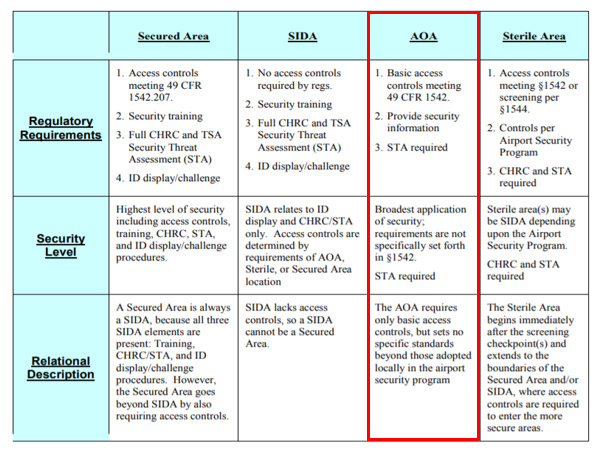
General aviation transient parking and T-hangars are usually located in the AOA. Each airport operator must carry out measures for controlling entry to the AOA to prevent and detect the unauthorized entry, presence, and movement of individuals and ground vehicles into or within the AOA. Although only basic access controls are required for AOA, the freedom of movement for general aviation transient pilots and passengers at commercial airports are limited because they lack locally issued security credentials. An airport’s access control systems and procedures are detailed, from an operational perspective, in each airport’s TSA mandated ASP.
Airport Credentialing and Physical Access Control Systems
Airport access control systems are normally considered in two parts: the first provides the vetting, approval and credential issuance process, and the second is a physical access control system that uses the resulting credential to provide or deny access. All individuals employed by or at airports require some sort of airport identification (ID) media to enter secure areas. Different types of ID media authorize different levels of unescorted access. The measures for controlling entry to the AOA must incorporate “accountability” procedures to maintain their integrity.
At large airports, physical access control systems (PACS) typically involve a computerized system such as credential/badge readers and automatic locks. However, at smaller airports, PACS can be as simple as lock-and-key methods or physical guards. Additionally, wireless technology, such as Near-field communication (NFC) and cloud computing, is convenient and often less expensive. NFC is an industry term for essentially using a smart phone and an app to be the electronic ID for the individual. NFC on smartphones has been utilized in the payment area for many years.
General Aviation Tenants
General aviation tenants should always be a part of an airport’s planning process for security-related matters that may affect their operations. TSA-regulated airports are required to designate an Airport Security Coordinator (ASC). The ASC is responsible for compliance with the ASP and is the point of contact for the airport’s security-related affairs.
General aviation tenants and pilots must be familiar with the local security protocols. When they are issued airport media badge, they should make sure to follow security procedures. At a minimum, pilots should always secure their aircraft using door locks and auxiliary locks, and secure all keys.
General Aviation Transient Pilots
Transient pilots lack locally issued security credentials and unescorted access authority. Therefore, airports must implement specific procedures to control access to general aviation transient ramps.
- General aviation transient pilots have a valid reason to be on a general aviation ramp.
- General aviation transient pilots carry credentials: FAA pilot certificate and government issued picture ID are required by the FAA.
- General aviation transient pilots, as FAA certificate holders, are vetted by TSA on a daily basis.
In addition, AOPA continues to promote AOPA Airport Watch program and educate general aviation pilots to be vigilant and report suspicious activities. General aviation pilots are usually familiar with behaviors of those who have a valid purpose for being at the airport.
The Importance of Alternative Airport Access for Transient Pilots
The impacts of security procedures on general aviation transient operations should be carefully considered and an ASP should be tailored to the airport’s unique operation. When the FBO is the only way that transient pilots can access the general aviation ramp, pilots should not have to purchase unnecessary services nor be charged a security fee. Otherwise, alternative airport access should be considered and implemented at public-use airports.
In addition to TSA, local, regional, or state authorities may impose various requirements affecting design of airport security systems and processes. The security environment varies with an airport’s geographic location. A Security Threat Assessment is required by federal regulations to determine threats for a given AOA. Based on the results of the local threat assessment, monitoring access to the AOA can be accomplished by a guard or a combination of access control systems and surveillance techniques. The level of security is usually applied to the entry point and not the exit point. In other words, entry and exit requirements do not have to be the same.
AOPA encourages creative solutions when airports design access control systems for general aviation ramps and parking.
Leveraging Airport Layout
It is recommended to exclude general aviation operations area from SIDA and commercial operations areas as much as it is practicable. If general aviation ramp is located independently from commercial operations areas, the “time and distance” concept could be considered to deter and delay the access of unauthorized individuals onto non-public areas of airports. Locating general aviation ramp independently from commercial operations helps avoid imposing commercial security procedures on general aviation operations.
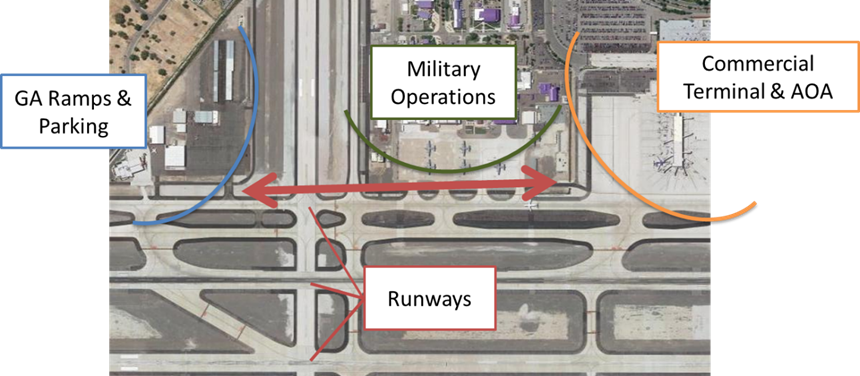
Gate Considerations
At some airports, a physical gate may be installed to separate general aviation ramp from commercial operations areas to minimize potential security conflicts. Both RTCA DO-230: Standards for Airport Security Access Control Systems and Safe Skies PARAS 0004: Recommended Security Guidelines for Airport Planning, Design, and Construction include sections on practical AOA boundaries. A physical gate not only prevents unauthorized entry to SIDA and secured areas but also allows different security procedures to be implemented in each operations area.

Technical Solutions
AOPA participates in RTCA Special Committee SC-224, Airport Security Access Control Systems, and helps maintain the industry standard document DO-230. This document provides guidance on acquiring and designing such systems, testing and evaluating system performance, and system operational requirements. DO-230 is updated annually to include the latest technologies and technical solutions. Examples include:
- Full-height turnstiles
- Automated Exit Lane Breach Control (ELBC) system
- Closed-circuit television (CCTV) and video surveillance systems
- One-time access codes
- Mobile devices as PACS credentials
Some technology solutions can be employed in conjunction with additional security layers such as identity verification and surveillance techniques. Full document is available here.

Most recently, AOPA proposed to include one-time access code considerations in DO-230, which will be included in the next revision DO-230J, scheduled to be published in 2019.
A one-time access code may be used instead of an airport access media card. This system can be implemented at a self-service fuel station. When a pilot purchases fuel using a credit card, a one-time gate access code will be printed on the receipt. This is the same concept used at gas stations to grant access to a carwash. Using a credit card device, a unique access code is issued to grant access to the gate controller.
AOPA stands ready to support and participate in local discussions.
Where can I find more information?
Individuals can reference guidance materials such as Standards for Airport Security Access Control Systems (DO-230I), National Safe Skies Alliance’s Recommended Security Guidelines for Airport Planning, Design, and Construction, and any recommendations issued by the Aviation Security Advisory Committee (ASAC).
Updated October 10, 2018